SD Card Bootloader by Backdoor Code Injection
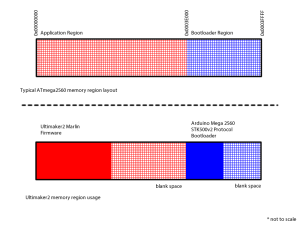
For various reasons, I decided to try writing a SD card bootloader for my Ultimaker2. The project is open source and on my GitHub here. My goal was to install this new bootloader without having physical access to the circuitry. Thus I cannot use a ISP tool and must be done through the bootloader that is already present on the Ultimaker2. The only way to do this is to partition off a portion of application memory region for a secondary bootloader that executes after the original bootloader. But the ATmega2560 has a restriction that prevents anything in the application memory region from modifying the flash memory at all. Overcoming this restriction is what this hack is all about, continue reading if you are interested in learning more. Popular open source 3D printers use a circuit that is derived from the Arduino Mega which is based on the ATmega2560 microcontroller. The Arduino Mega 2560 edition uses an open source STK500v2 protocol bootloader. Typically, on AVR microcontrollers, you may only edit the bootloader using a ISP tool or debugger. The bootloader should not modify itself, because if a bootloader corrupts itself, the entire circuit will be bricked, as the bootloader won’t be able to recover itself if it is already corrupted. In this case, only a ISP tool can be used to restore it. Memory Layout of the ATmega2560 This represents the memory usage of the ATmega2560 Important to note: any code executed inside the application…